如何保护小部件免受伪造请求
时间:2023-09-07问题描述
假设您有一个 JavaScript 小部件,当且仅当用户想要单击它时,它才需要向您的 Web 应用程序发出请求.您不希望此请求易受 CSRF 攻击,因此您将 iframe 写入页面.根据源继承规则,父站点将无法读取 CSRF 令牌.但是点击劫持(或 likejacking )呢?由于 CSRF,您必须在 iframe 中,并且对于 x-frame-options 无能为力,并且frame-busters 也是如此.
Lets say you have a JavaScript widget which needs to fire off a request to your web application if and only if the user wants to click on it. You don't want this request to be vulnerable to CSRF so you write an iframe to the page. Based on the origin inheritance rules the parent site won't be able to read the CSRF token. However what about clickjacking (or likejacking )? Because of CSRF you must be within an iframe and there for the x-frame-options cannot help, and the same holds true for frame-busters.
攻击者将在小部件加载后对 iframe 应用 SVG 掩码.此蒙版将使 iframe 不可见.此时,攻击者可以将 iframe 的大小调整为页面大小,或者让这个现在不可见的 iframe 跟随光标.无论何时用户点击页面上的任何位置,iframe 都会收到点击事件并结束游戏.
The attacker is going to apply an SVG mask the iframe after the widget has loaded. This mask will make the iframe invisible. At this point the attacker can either resize the iframe to be the size of the page or have this now invisible iframe follow the cursor. Either way whenever the user clicks anywhere on the page, the iframe receives the click event and its game over.
所以有一个二元性,你似乎被困在 CSRF 和 Clickjacking 之间.这个问题的最佳解决方案(如果有的话)是什么?
So there is a duality, it seems you are stuck between CSRF and Clickjacking. What the best solution (if any) to this problem?
推荐答案
点击widget需要打开一个包含新页面的弹窗——iframe不行,必须是新窗口——这完全在您的 Web 应用程序的控制之下.在该页面上确认操作,无论它是什么.
Clicking on the widget needs to open a pop-up window containing a new page -- an iframe is not good enough, it must be a new window -- which is entirely under the control of your web application. Confirm the action, whatever it is, on that page.
是的,这有点不雅,但目前的 Web 安全架构并没有给您任何更好的选择.
Yes, this is somewhat inelegant, but the present Web security architecture doesn't give you any better options.
这篇关于如何保护小部件免受伪造请求的文章就介绍到这了,希望我们推荐的答案对大家有所帮助,也希望大家多多支持跟版网!
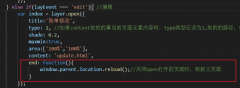 layer.open打开的页面关闭时,父页面刷新的方法layer.open打开的页面关闭时,父页面刷新的方法,在layer.open中添加: end: function(){ window.parent.location.reload();//关闭open打开的页面时,刷新父页面 }
layer.open打开的页面关闭时,父页面刷新的方法layer.open打开的页面关闭时,父页面刷新的方法,在layer.open中添加: end: function(){ window.parent.location.reload();//关闭open打开的页面时,刷新父页面 }