<bdo id='5v2Kv'></bdo><ul id='5v2Kv'></ul>
|
<legend id='5v2Kv'><style id='5v2Kv'><dir id='5v2Kv'><q id='5v2Kv'></q></dir></style></legend> | | |
<tfoot id='5v2Kv'></tfoot>
|
|
| |
|
|
<i id='5v2Kv'><tr id='5v2Kv'><dt id='5v2Kv'><q id='5v2Kv'><span id='5v2Kv'><b id='5v2Kv'><form id='5v2Kv'><ins id='5v2Kv'></ins><ul id='5v2Kv'></ul><sub id='5v2Kv'></sub></form><legend id='5v2Kv'></legend><bdo id='5v2Kv'><pre id='5v2Kv'><center id='5v2Kv'></center></pre></bdo></b><th id='5v2Kv'></th></span></q></dt></tr></i>
| | <small id='5v2Kv'></small><noframes id='5v2Kv'>
|
|
|
|
本文介绍了前端敏感信息的处理方法,对大家解决问题具有一定的参考价值,需要的朋友们下面随着跟版网的小编来一起学习吧!
问题描述
我正在构建我的第一个 react 应用,但不确定前端的安全性.我正在调用以下第三方库:emailjs.sendForm(serviceID, templateID, templateParams, userID);userId 字段是敏感信息.我对我的 onSubmit 处理程序进行了以下调用.我想知道我是否需要以某种方式保护这些信息?另外,有没有办法让我检查用户是否能以某种方式看到这些信息,我以某种方式检查并找到方法中的代码?
emailjs.sendForm(邮箱",客户电子邮件",#形式",**here_is_the_sensitive_info**").then(() => {重置表格({});}).catch(() => {常量确认 = document.createElement("H6");acknowledgement.innerHTML = "出了点问题,请尝试.";document.getElementById("form").appendChild(acknowledgement);});
解决方案
在这种情况下,EmailJS 是要在浏览器中使用的,所以我认为 userId 不敏感全部.
在自己的文档中,可以看到如下入门说明.
<块引用>
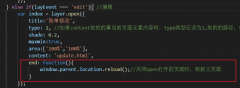 layer.open打开的页面关闭时,父页面刷新的方法layer.open打开的页面关闭时,父页面刷新的方法,在layer.open中添加: end: function(){ window.parent.location.reload();//关闭open打开的页面时,刷新父页面 }
layer.open打开的页面关闭时,父页面刷新的方法layer.open打开的页面关闭时,父页面刷新的方法,在layer.open中添加: end: function(){ window.parent.location.reload();//关闭open打开的页面时,刷新父页面 }
 layer.open打开的页面关闭时,父页面刷新的方法layer.open打开的页面关闭时,父页面刷新的方法,在layer.open中添加: end: function(){ window.parent.location.reload();//关闭open打开的页面时,刷新父页面 }
layer.open打开的页面关闭时,父页面刷新的方法layer.open打开的页面关闭时,父页面刷新的方法,在layer.open中添加: end: function(){ window.parent.location.reload();//关闭open打开的页面时,刷新父页面 }